How do I connect and manage Kubernetes cluster from POD using nsenter utility
I am using multi node Kubernetes cluster. I am using following YAML to connect and manage host machine.
apiVersion: v1
kind: Pod
metadata:
name: my-nsenter-test
spec:
hostPID: true
hostNetwork: true
hostIPC: true
containers:
- name: my-nsenter-test
image: ubuntu:18.04
command: ["tail"]
args: ["-f", "/dev/null"]
securityContext:
privileged: true
But I would like to connect and manage multi node cluster (any other node in the cluster) using single POD.
Short answer: You can connect from the pod using nsenter utility to the only one node - the node that pod is hosted on, but better don't do that because deploying pods with wide permissions is against best security practices.
You can't connect to the other nodes, as pod is hosted on only one node. Setting host... fields means that they are only sharing resources with the host - one host node and simply it's not possible to achieve it using nsenter utility.
This diagram is good representation of the Kuberentes architecture related to pods and nodes:
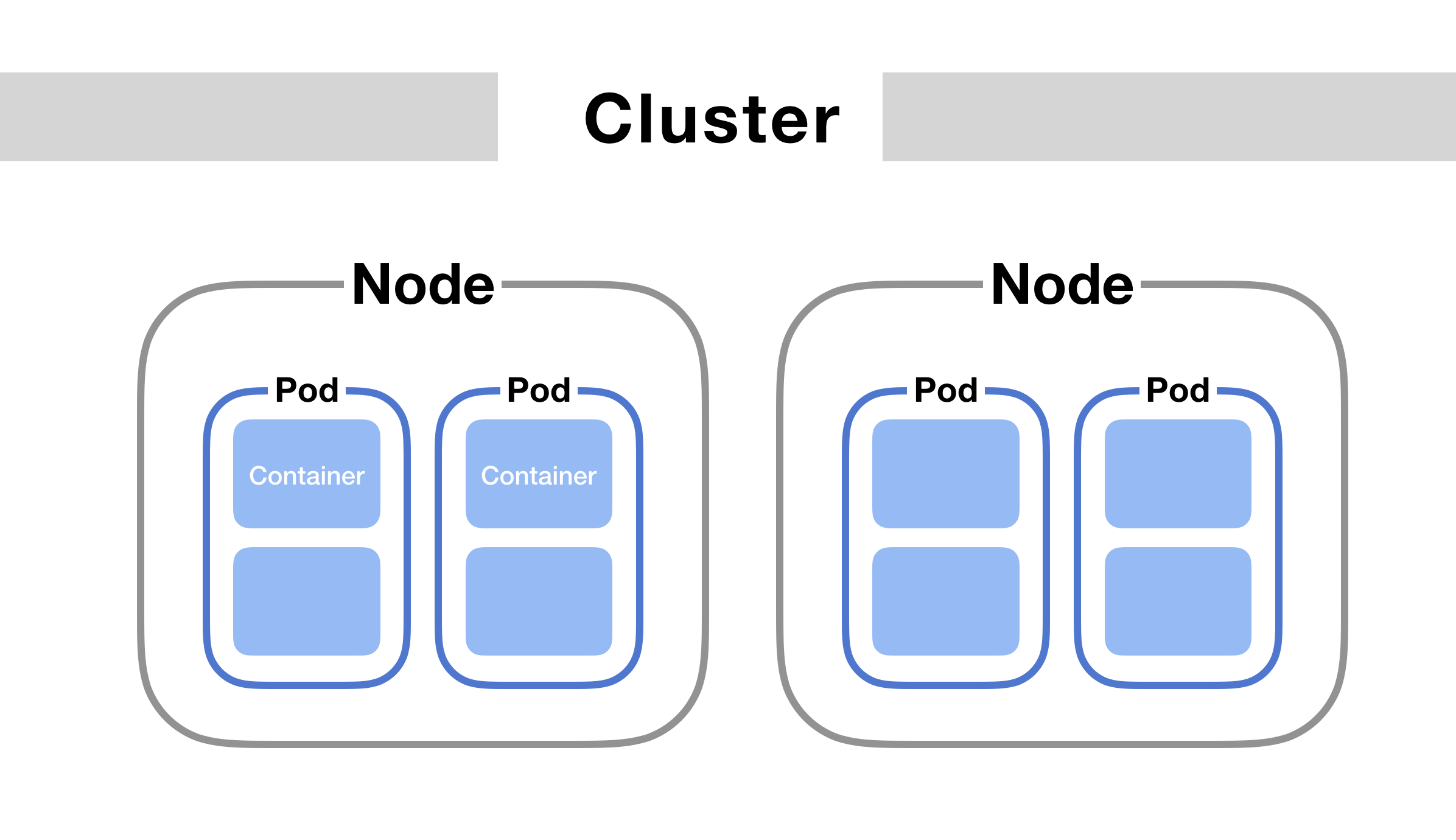
For connecting to the host node just run following command:
kubectl exec -it my-nsenter-test -- nsenter --target 1 --mount --uts --ipc --net /bin/bash
Avoid using privileged policies and hosting common resources with the host
Generally this approach for managing hosts is against best security practices.
Giving pod wide permissions is strongly not recommended, this leads to many security concerns, usually it's granting broader permissions that intended:
The way PSPs are applied to Pods has proven confusing to nearly everyone that has attempted to use them. It is easy to accidentally grant broader permissions than intended, and difficult to inspect which PSP(s) apply in a given situation.
Also check this article - Securing a Cluster.
- How can I pass the variables I have placed in the .env file to the containers in my docker swarm?
- Lots of "Uncaught signal: 6" errors in Cloud Run
- How to enable nginx reverse proxy to work with gRPC in .Net core?
- How to configure docker CLI to access docker server from minikube on Git-Bash?
- ALERT: [pool www] user has not been defined when using thecodingmachine/php:7.1-v3-fpm-node10
- How to check rabbitMQ connection(health check) up or not?
- Can't connect adminer to postgres server in docker
- Docker: adding a file from a parent directory
- The Bitnami InfluxDB container automatically exits
- How do I recreate docker-daemon's additional iptables rules?
- Alpine Dockerfile advantages of --no-cache vs. rm /var/cache/apk/*
- Python package install fails on docker image python:3.11-alpine : Error compiling cython file
- How to connect to Nvidia MPS server from a Docker container?
- SQL Server docker container stop after initializing
- Fallback for environment variables with docker-compose
- PHP/Symfony is very slow in Docker setup
- Chrome failed to start in docker container using Selenium after upgrading to ChromeDriver v80 and Chrome v80
- How to keep the ENTRYPOINT but replace CMD of a docker image from a gitlab pipeline
- App crash when prepare to deploy using docker-compose
- How to easily install and uninstall Docker on macOS
- How to fix 502 Bad Gateway error in nginx?
- InfluxDB 2.0 Client Stops Writing After Few Hours (Notifications Still Received, Container Restart Fixes Temporarily)
- Docker Compose stuck downloading or pulling fs layer
- docker.sock permission denied
- How to delete cached/intermediate docker images after the cache gets invalidated?
- Stop Synology notification "Docker container stopped unexpectedly"
- Runtime Error: No Running Event Loop on Streamlit with Docker
- Improving docker build time for pip based python application
- How to create named and latest tag in Docker?
- The body in request is returned in response