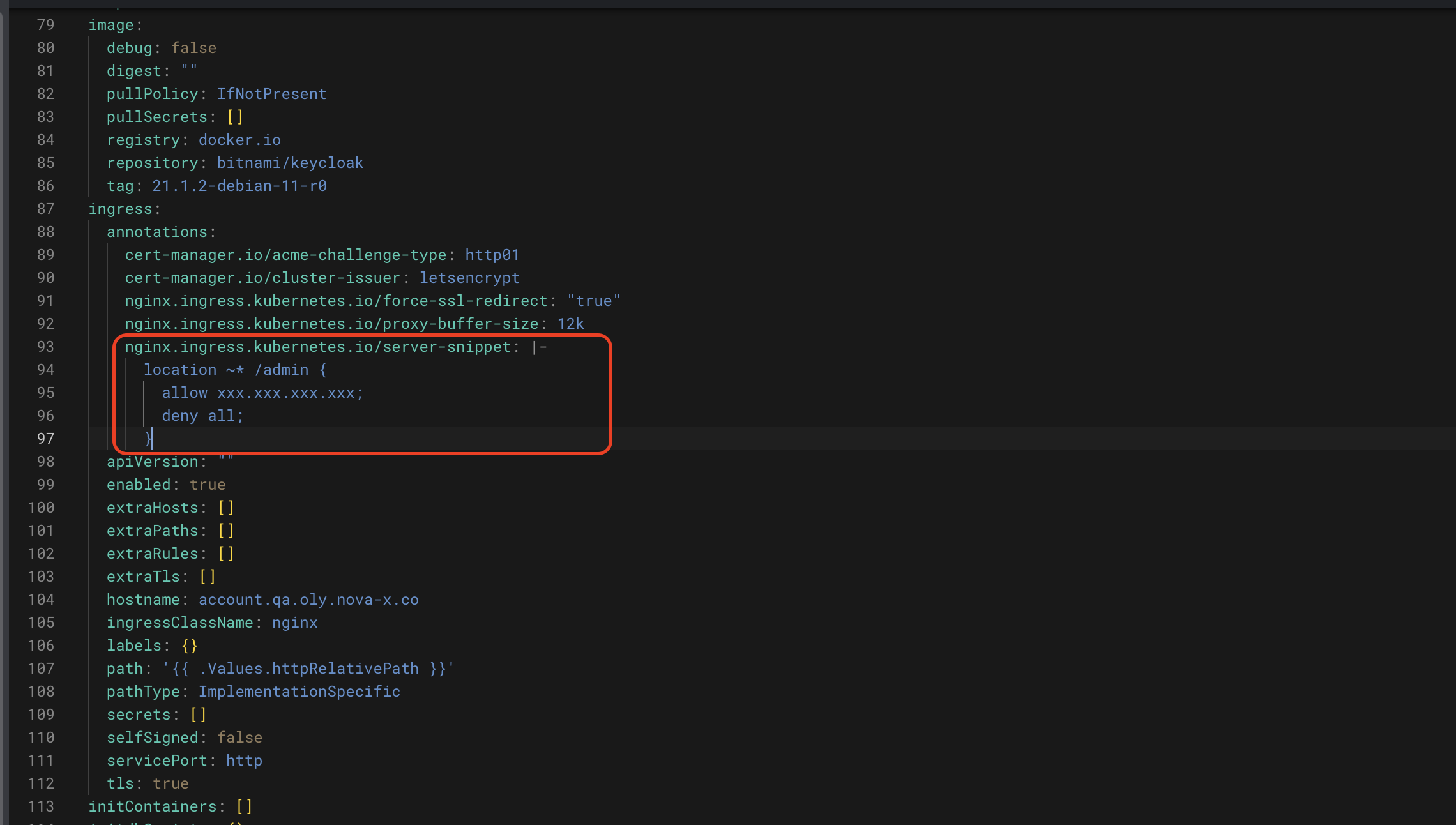
How to restrict access to Keycloak admin console to a specific IP/IP range?
Is there any way to restrict the access to the keycloak admin console by IP / IP Range? I have deployed the Keycloak in Azure Kubernetes that uses Nginx Ingress controller. So, I tried to restrict as highlighted below
but it blocks everything. I would assume that Ingress receives the incoming request from the Azure Kubernetes Load balancer so it does not consider the client IP to allow access.
How do I restrict the access to the keycloak admin console by IP / IP Range?
Update#1: I believe that the above configuration to restrict the path by the IP / IP Range is effective expect that it redirects the coming request to a non-existing location
xxx.xxx.xxx.xxx - - [30/Aug/2023:15:42:25 +0000] "GET **/admin/** HTTP/2.0" 404 548 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.0.0 Safari/537.36" 507 0.000 [-] [] - - - - bfbe1faa35dcc40e82e5e22bd557cf96
2023/08/30 15:42:25 [error] 1171#1171: *6809656 **"/usr/local/nginx/html/admin/index.html"** is not found (2: No such file or directory), client: 173.32.206.145, server: account.qa.oly.nova-x.co, request: "GET /admin/ HTTP/2.0", host: "xxxx"
I was expecting this to apply just the IP based filter but not change the existing behaviour.
You can use loadBalancerSourceRanges on the service as mentioned here.
To restrict traffic for a certain path use location-snippet instead of server-snippet as detailed in this answer.
- How do you find the cluster & service CIDR of a Kubernetes cluster?
- Minikube not pull image from local docker container registry
- docker desktop Preferences settings page is not loading and state is docker desktop is starting from forever
- How do I switch between contexts in K9s when the contexts have already been set up?
- Is it possible to change subnet in Azure AKS deployment?
- When deploying a Laravel Octane app with Swoole on Kubernetes (or AWS ECS), is a separate Nginx container required alongside the Octane app?
- How to merge kubectl config file with ~/.kube/config?
- How to add swap memory in kubernetes pods?
- How to add a tty on pod?
- How to override a helm value
- Where do docker images' new Files get saved to in GCP?
- Is there an option to copy image between nodes in kubernetes cluster?
- How to start an Ingress Controller with flags? (microk8s)
- How do I get a single pod name for kubernetes?
- Error No agent available while doing kubectl exec/logs
- How to change AKS cluster networking from Kubenet to Azure CNI?
- How to attach a service account to a GKE deployment/servic like you can an ECS service?
- Wait for kubernetes job to complete on either failure/success using command line
- How to find the url of a service in kubernetes?
- Can I have multiple values.yaml files for Helm
- Kubernetes POD delete with Pattern Match or Wildcard
- Does NodePort route traffic only to pods that are hosted under node to which we send request? How to achieve that if it's not the case?
- How to ensure kubernetes cronjob does not restart on failure
- @prisma/client did not initialize yet. Please run "prisma generate" and try to import it again
- Failed to bind properties under 'server.address' with helm
- Kubernetes : How to scale a deployment from another service/pod?
- How to prioritize node pools in GKE for autoscaler when using multiple spot instance node pools with different machine types?
- YQ: load a text file as array and use it for an operation
- kubernetes pod memory - java gc logs
- what is gotk notation/symbol means in the fluxcd